
Fortified Phishing™
Are your employees prepared for a Phishing Attack?
What is Fortified Phishing™?
Fortified Phishing™ enables you to evaluate employees’
security awareness.
It simulates phishing campaigns and detects easy clickers that can place your organisation at risk. Increasing their awareness and vigilance will reduce your cyber exposure and help you to prevent data breaches, minimise malware-related downtime, and avoid crippling incident costs.
Why use Fortified Phishing™?

What is a Phishing Attack?
Phishing is a cyber attack that uses disguised email as a weapon.
Phishing attacks use social engineering to mimic trusted entities and increase the likelihood of the recipient to act, such as clicking on a malicious attachment or link and unwittingly enter sensitive information such as a password or bank account details.
A successful phishing attack enables cyber criminals to infiltrate and compromise business networks.
What a Phishing Attack Looks Like:
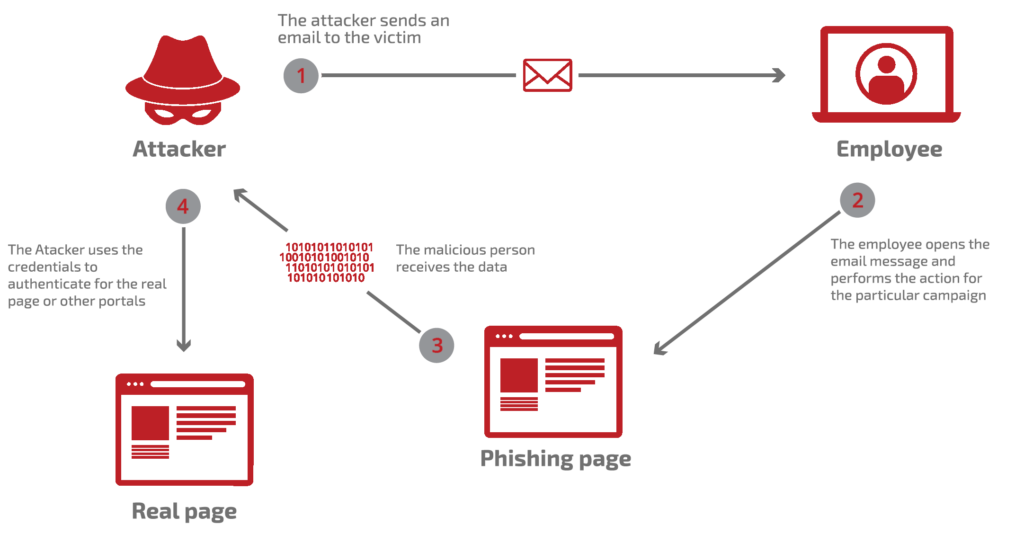
- Phishing emails are sent from the Fortified Phishing™’s cloud platform to a list of emails the customer chooses.
- None of the emails contain real malicious content (ransomware, URLs, worms, etc.).
- Events are tracked and updated by the Fortified Phishing™ platform, throughout the campaign.
- Fortified Phishing™ utilises a range of email templates, attachments, and login pages, to create a range of sophisticated attacks to test your organisation’s preparedness and resilience to a phishing attack.
Actionable Insights
Each step in the campaign is tracked (e.g. when an email is opened, and a link is clicked) to provide your organisation with the full picture of your employees’ security awareness levels and focus on employees that require more education and monitoring than others.

Next Steps
We always recommend a scoping call to discuss the company, your current security posture and the options to choose from.
Please use the booking calendar, below, to schedule your scoping call:
